 UAC, the impetus behind the famous Mac commercials, and the biggest frustration in Vista does have some reasoning behind it. One is that Microsoft wanted to allow non-techies to be able to use their computers without having admin rights. This is generally good. Techies that complain about UAC aren’t complaining just because of an extra step in getting a job done. They’re complaining because UAC is so annoyingly stupid:
UAC, the impetus behind the famous Mac commercials, and the biggest frustration in Vista does have some reasoning behind it. One is that Microsoft wanted to allow non-techies to be able to use their computers without having admin rights. This is generally good. Techies that complain about UAC aren’t complaining just because of an extra step in getting a job done. They’re complaining because UAC is so annoyingly stupid:
– If you right-click on an item on the start menu and select “Run as Administrator”. It then prompts, “Cancel/Continue?”. It’s like when you asked your Mom for a glass of water and she replies, “I can’t hear you”, and you then had to reply, “May I have a glass of water, please?”
– Similarly, typing “regedit” at the command line forces the prompt. I specifically typed 7 characters and pressed return, does another mouse click really help?
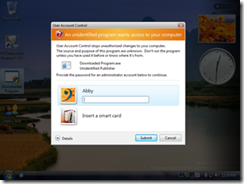
Of course, the Microsoft engineers aren’t dumb, they did this on purpose; and the reason is usually misunderstood by those writing about UAC. Notice that when you are prompted for the privilege elevation, the entire screen dims, and the only window usable is the security prompt? Jesper, like many others, writes that UAC has nothing to do with malware. But this is not true! The elevation prompt screen is in a locked-down UI state; non-privileged programs are denied access to the UI at this time. This prevents a virus from moving your mouse to administrative programs or from typing “regedit” at your administrative prompts. It also prevents a trojan from displaying a dialog that *looks* like the UAC screen and getting you to type your password into it. This is why ItsVista noted that they couldn’t issue a print screen command on the elevation prompt. The malware countermeasures of UAC are much better described in this article from Microsoft.
Contributing to the confusion about UAC is that Microsoft employees have watered down the feature by implying that it’s not a security feature; Mark Russinovich writes,
“Because elevations and ILs don’t define a security boundary, potential avenues of attack , regardless of ease or scope, are not security bugs.”
I suspect this is lawyer talk; I don’t really understand it. To claim that all this good work isn’t security either means that you know there is a big hole in it (possible), or that a lawyer said not to describe it as a security feature so you don’t get sued. Jim Allchin likewise had some watered down comments about UAC here. Both claim that the only ‘secure’ way to prompt is to use Ctrl-Alt-Del. They are probably right. Windows has the fundamental security flaw that it allows one process to see the keystrokes and mouse events destined for another. This design flaw (also a flaw in many other windowing systems), is ultimately the reason we have UAC today.